Overview
In the previous part, we looked at some of the concepts behind switch operation. In this chapter, we will continue with the configuration and verification of the basic switch configuration, configure and verify port security on a switch and learn some other important concepts.
Duplex settings
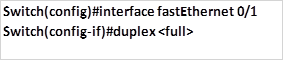
As we mentioned in part 1 of this chapter, the duplex mode determines whether communication will be unidirectional or bidirectional. By defaults, the duplex on CISCO switches is usually auto. This means that if one side is operating on half-duplex, then the port would be in half-duplex as well.
We can hard code the ports on the switch to use only full duplex since it is the preferred mode. The commands needed are implemented in the interface configuration mode on a switch as shown below.
Port security
There are several security breaches that switches are vulnerable to. In this course however, you are only expected to understand some basic security options such as port security.
There are several attacks that switches are vulnerable to such as:
MAC address flooding – in this type of attack, an attacker usually gains access to a switch using a node. They then use a tool to send invalid source MAC addresses to the switch. Switch operation works by adding the MAC address to the mac-address-table which is limited to a certain number of MAC-addresses. When this database is filled up, the switch is unable to forward traffic using unicast and it begins to operate like a hub by flooding frames out of the ports. This means that the attacker can see all the frames for the nodes in the network.
MAC-address spoofing – in this attack, an attacker poses as a DHCP server, when legitimate clients request for addresses from the DHCP server, the attacker responds with an address that would permit them to see the traffic from a particular node.
Other common attacks may be aimed at CDP, telnet or other technology weaknesses that may be manipulated through the switch.
Using port security is one way to protect the switch against such attacks. All switch ports or interfaces should be secured before the switch is deployed. Port security limits the number of valid MAC addresses allowed on a port.
Secure MAC Address Types
Port security is one way of securing a CISCO switch. Configuration options using port security can secure the switch in the following ways.
- Use of statically configured MAC addresses: this entails assigning each port on a switch to a particular user node by hardcoding the user’s MAC address to the port. This means that only devices matching the configured MAC addresses can communicate. This is a good way to implement security, however, it may be an administrative nightmare to configure the MAC addresses of the clients to the switch due to the size of the network.
- Using dynamic secure MAC addresses is a good way to ensure security on a switch. The switch ports are configured to learn and store the MAC addresses of the user nodes.
- Using sticky MAC addresses is a good way to ensure that only dynamically learnt MAC addresses can use the switch, these addresses are then saved to the running configuration file of the switch which means that they are lost when the switch is rebooted.
-
We can also specify the maximum number of MAC addresses that can access a particular port. This is a good way to secure against MAC address spoofing.
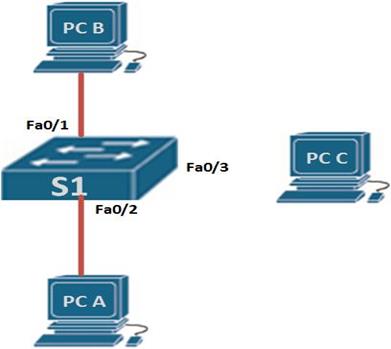
In this case we will be using a modified topology to configure port security. The topology shown below consists of 1 switch and three host nodes. PC A, PC B and PC C. we have connected only PC A and PC B to the switch and we will use PC C as the test for security.
When configuring port security, there are several Security Violation Modes that are used to protect the switchports.
Security violations
The security violations determine the action to be taken if access on a port does not meet certain criteria.
The violations apply when the maximum number of user nodes that can access a port is reached, when a particular MAC address that has not been learnt dynamically or statically tries to access the switch or other criteria that may be configured according to the security policies in place in an organization.
The violations that can be triggered due to these events include:
- Protect – in this mode, the switch will drop the frames from a node that breaches security, however, it will not inform the administrator of the security breach.
- Restrict – in this mode, if a violation of the security policies is made, the port drops the frames from that port and records the breach. In most cases, this entails sending an SNMP trap, increasing a violation counter, and sending a syslog message.
- Shutdown – when a violation is detected, the port that the frames were received on is shut down. The switch also sends a message to the administrator using s SNMP and syslog. The violation counter also records the breach. In this mode, the administrator is the only one who can re-activate the port after investigating the breach.
In our scenario, we will configure port connected to PC A as security violation restrict, the port connected to PC B will be in violation mode restrict and port Fa0/3 will be in violation mode shutdown.
To configure the secure ports as we have mentioned above, follow the steps shown below.
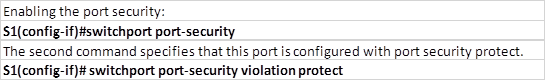
Step 1.Configuring port security protect on port fa0/1.Enter the configuration mode for interface fa0/1

Step 2: in the interface mode, enter the following commands to activate port security and then enable the protect violation mode:
Step 3. We need to bind the mac address of PC A to port fa0/1 such that if another node is connected to this port, the interface will deny this port from transmitting. To do this, we will configure the port with a static mac address of PC A. as shown below.

The mac address keyword is the configured mac address on the PC’s NIC.
Step 4: is the final step is to specify the number of MAC addresses that can access this port. In our case we will specify only one so that if any other device tries to access this port, the port will be protected.

In our case we use 1.
After this configuration, save the configuration to the NVRAM.
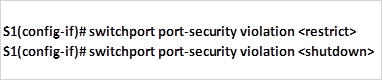
To configure port security violation restrict and shutdown, the commands are shown below.
We can also configure the type of mac addresses we would like to access a specific port. Using the static mac address is good but can be tedious in a network with thousands of mac addresses.
In this case we use sticky mac addresses, this means that when a node is connected on a switchport, it’s mac address is learnt and stored in the switch’s memory. To configure sticky mac addresses we use the command:

It is recommended that you should also configure the maximum number of mac addresses on a port so that no one can use other devices such as hubs.
Now that we have configured port security on the two ports, we need to verify their operation.
On port fa0/1, we have configured the port for violation mode protect and on port fa0/2 we have used the violation mode shutdown. Both ports are configured with nodes.
The command show port-security <int type and number>, shows the protection status on a port. The output of this command for port fa0/2 is shown below.
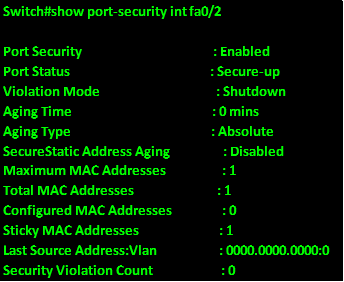
As you can see from the output above the port security is enabled and the port is shown as secure. The violation status is shutdown and there is one sticky mac address that has been learnt by this interface.
To see whether this security will work, we will connect PC_C to this interface and view the output of this command. The output is shown below.
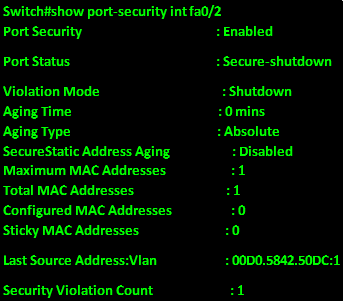
As you can see from the output above, the violation count moved from 0 to 1 and the port status is shown as “secure-shutdown” meaning that it has been deactivated till an administrator intervenes.
With this configuration, we have finished the security configuration options that we need to configure on our switches. In the next section, we will look at the various verification and troubleshooting commands that you need to know when configuring a switch.
Verification and troubleshooting commands
There are several commands that can be used to verify the operation of a switch as well as to troubleshoot when there is a problem. Some of these commands we will discuss later as we continue with switching but some of the basic ones are shown below. 
Show running-config
Just like on routers this command will show the configuration that is currently in use on the switch. The output of this command on S1 is shown below.
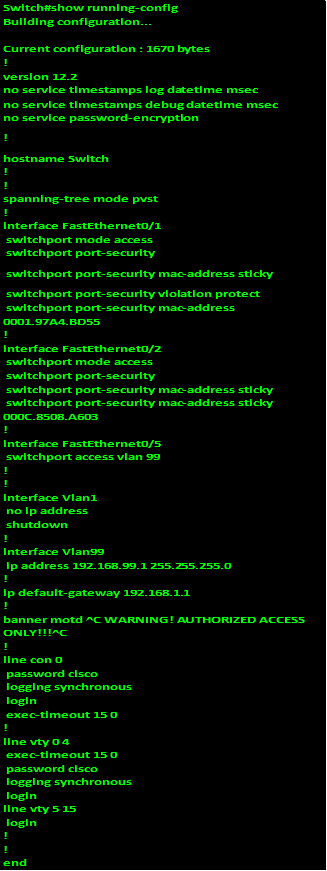
With this command, you can be able to view most of the configuration options that have been made on the switch. This command can be useful when verifying whether the configuration commands that were used are correct.
Show mac-address-table
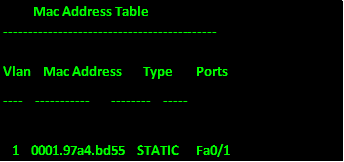
This command will show all the mac addresses that the switch knows about. It can be useful when you want to verify whether the switchports have nodes on them. Since we have configured only 2 ports on our switch, the mac address table will only have 1 entry with the mac addresses of the two PCA since the port attached to PC 3 as we configured was shutdown due to a violation, this is as shown below.
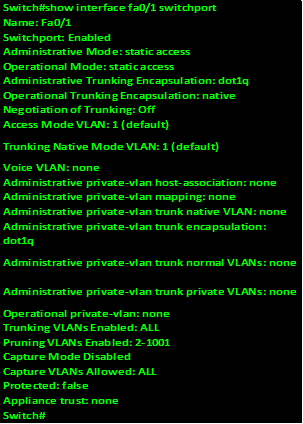
Show interface <name and number> switchport
This command will show various statistics for the switchport. More of this will be discussed in later chapters.
Summary
In this chapter, we have looked at the various configuration options for security on switch ports, we have also looked at various verification commands. In the next chapter, we will look at VLANS. This chapter is supposed to introduce you to the concepts behind switch operation, as well as basic switch configuration.
The concepts in this chapter are an integral part of the ICND 1, ICND 2 and CCNA composite exams. In the next chapter, we will look at a topic that is at the heart of switch operation which is VLANs.

