Overview
In the previous chapter we were introduced to computer networks and we got to know their importance in everyday lives. In this chapter, we will look at the layered models that are used in communication over networks.
We will discuss the TCP/ip model and the OSI model to better understand how communication works. This will lead into detailed discussion on each of the layers so as to better understand them.
Use of layered models
To better understand the various protocols and how they work with each other, we use layered models. A layered model shows how the protocols work at each layer as well as how the layers interact with the layers either above them or below them. The layered models that are used in modern computer networks are two; the OSI model (Open Systems Interconnection) and the TCP/IP model (Transmission Control Protocol/ Internet Protocol)
There are several benefits that to using the OSI and TCP/IP models in explaining how network protocols work and these include the following.
- Each layer in a model defines different protocols, therefore by using a layered model, network engineers can be able to define and design protocols which conform to the specific layer.
- Competitions between different vendors is increased, this is because the models define standards and therefore product superiority is not based on the use of certain protocols since all products support them.
- The layered model is useful since it allows for independence between other layers. This means that if a change in technology or capabilities is made in one layer, it will not affect another layer either above it or below it.
- Since the layered model is an open standard, it provides for conformity and interoperability between different networking devices.
As mentioned earlier, the two models that we will be discussing in this course are the OSI and the TCP/IP models. However, these two models are different.
The TCP/IP model is protocol model and it describes the functions at each of its layers. The protocols that are defined in this model are usually based on vendor specifications. However, the TCP/IP model is an open standard and therefore no company has control of the definitions. This protocols and definitions in TCP/IP, are maintained in public records maintained by the IETF (Internet Engineering Task Force) and they are known as RFCs (Requests for Comments). The TCP/IP model was introduced in the 1970’s by the US’s DOD (Department Of Defense).
NOTE: although you are not required to know all the background information, you will be expected to understand some of the RFC’s for the course as well as the CCNA examinations.
The OSI model is a reference model and it is used to provide or maintain consistency and standardization among the various protocols and services that are used in networks. It does not give strict regulations on how or what protocols and services should work at each layer, rather, it works as a guideline. A good analogy would be a city’s building regulations committee, this body would be in charge of the regulations on where a person can put up a structure, the strength specifications, the maximum height and other regulations, however, it cannot prescribe the specific design of the building to be put up. The reference model is aimed at giving clear understanding of what happens – the functions and processes at each layer, however, it does not say exactly how they should be implemented.
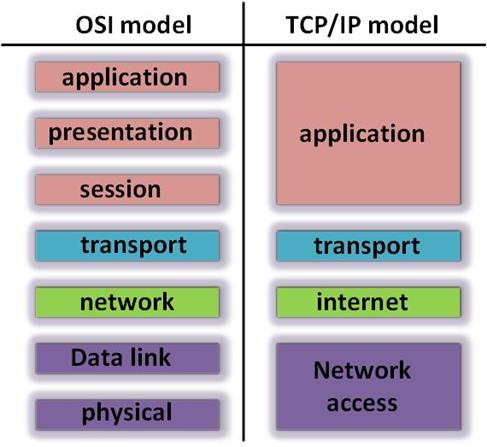
The OSI and TCP/IP models are shown below, however, the OSI model is the most commonly used model in today’s networks. Network engineers use it in designing, operating and troubleshooting networking equipment where necessary. This does not mean that the TCP/IP model is not relevant as we will see as we proceed in this course.
TCP/IP model
This model was first introduced in the 1970’s. There are four categories as you can see from the output above. Network communications were first defined using this model and for successful communication to occur, the functions of each layer must be in place in a network.
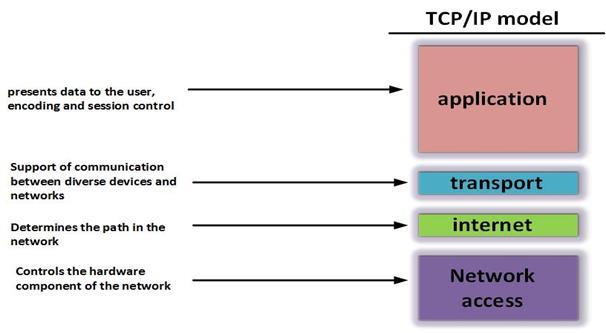
From the output below, you can see the function of each and every layer of this model. The application layer, is the component that interfaces with the user, when you are using a web browser, this is a component of the application layer.
The transport layer defines the various ports and helps differentiate the different types of communication from a single user. You may be sending an email, browsing and listening to internet radio on one computer. It is the work of the transport layer to differentiate the different types of communications. The transport layer also helps in interoperability between different network devices such as a PDA and a computer.
The internet layer is meant to provide the best path to remote networks, this differentiates the different devices on a network. If a message is to be sent from one computer to another on a remote network, it is the work of the internet layer to make sure the message gets to the intended recipient. You may compare the internet layer to an address you use when you want to send a letter.
The network access layer acts as an interface between the hardware and software components in the network. The application, transport and internet layers are all implemented by software, however, the network access translates the messages from these layers to a form that can be transmitted over various media such as fiber optic cables, copper wire and wirelessly.
The protocols that are defined in the TCP/IP model describe the various functions and processes at each layer. This means that the protocols at each layer have to have specific functions as described by the TCP/IP model.
If we want to send an email, for example, the steps shown below would be the functions of each layer for this communication.
- At the application layer, we would create the email and this would be the data that would be communicated over the network.
- The transport layer would then break this data into segments and add information in a process known as encapsulation.
NOTE: encapsulation is a process of adding protocol specific information as well as converting a protocol data unit (PDU) into a form that conforms into the layer it is in. in this case, the PDU at the transport layer is the segment.
- The segments would then be passed down to the internet layer and encapsulated into packets, in this layer, logical addressing would be added. (more on logical addressing will be discussed later)
- The packets would then be passed to the network access layer, the network access layer would then prepare the packets for transmission over the physical media such as fiber optic cable by converting the data to light signals.
- When the data is received at the destination, the reverse process would happen, i.e., removal of protocol specific information – decapsulation as well as reassembly into the application data would be carried out.
- The data would then be passed to the user. This process is illustrated below.
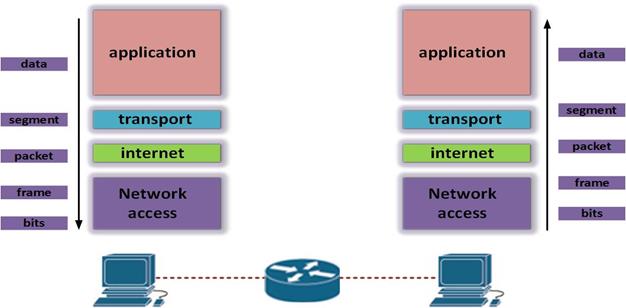
As mentioned above, each form that the data takes at each layer of the TCP/IP model is known as a PDU, we have already discussed the transport and internet layer PDUs. The list below shows each of the PDUs at the different layers of the TCP/IP model.
- Data – the end user information, this may include, email content, website information among others. This is the information presented to the user.
- Segment – as mentioned earlier, this is the PDU at the transport layer.
- Packet – in the internetwork layer, the packets are the PDUs and they include the logical addressing for remote delivery.
- Frame – this is the form that data at the network access layer takes, there is also addressing at this layer which is physical addressing such as the MAC address.
- Bits – the form that is carried over the physical media form is Bits, these may be in many forms such as electrical signals, light signals and others.
OSI model
The OSI model provides an extensive list of functions and services that can occur at each layer. It also describes the interaction of each layer with the layers directly above and below it.
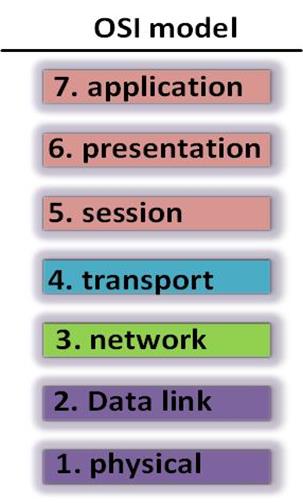
Comparison of TCP/IP and OSI models
The protocols that are discussed in the TCP/IP model, can be clearly defined and described in the OSI mode. In this model, as shown in the diagram above, the application and network access layer are broken down to define more functions. The application layer is broken into the application, presentation and session layers, while the network access layer is broken up into the data link and the physical layers.
The OSI model shows more detailed functions of each of these layers unlike the TCP/IP model. At the data link and physical layer, the OSI model only describes how data is handled from the network layer to the physical layer. It does not state what exactly happens at each of them.
The network and transport layers of the OSI model are very similar to those of the TCP/IP model. The functions at these layers are the same.
The transport layer defines how communication between different user machines happens. At this layer, the rules define how messages are acknowledged, how the communication recovers from errors, and how the segments are arranged. In the OSI model, the protocols that mainly work here are the UDP and TCP protocols. We will look at these in future topics.
PDUs and communication over a layered model
The OSI model defines how messages are encoded, formatted, encapsulated, and segmented so that they can be transmitted over networks. As we mentioned earlier, the data is usually broken down into different PDUs and the layers in the OSI model define how each PDU is controlled so as to make communication successful.
Addresses are one of the ways that communication is made successful in the network. If we can use the post office analogy, you can imagine how difficult it would be if not impossible to send letters without a destination address or how difficult it would be if the recipient would not know who to reply to. The diagram below shows the various addresses that are used in communication over the network.
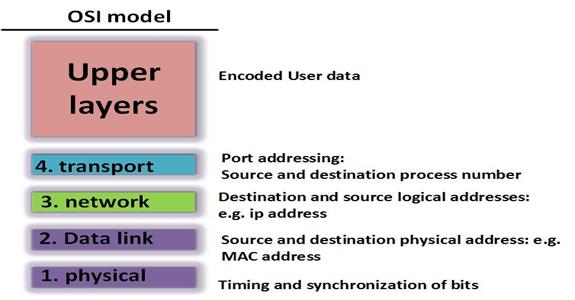
The use of each type of address, will be discussed in subsequent chapters. The PDUs define the type of data at each layer of this model.
NOTE: the process of transmitting data on the network is guided by the TCP/IP and OSI reference models therefore you should not ignore these concepts since they are crucial to understanding communication over the network.
Summary
In this chapter, we have discussed how communication works over the layered model. We have looked at the TCP/IP and OSI reference models and how they define communication at each layer. We have also looked at the protocol data units and compared the two models. In the next chapter, we will look at the application layer.