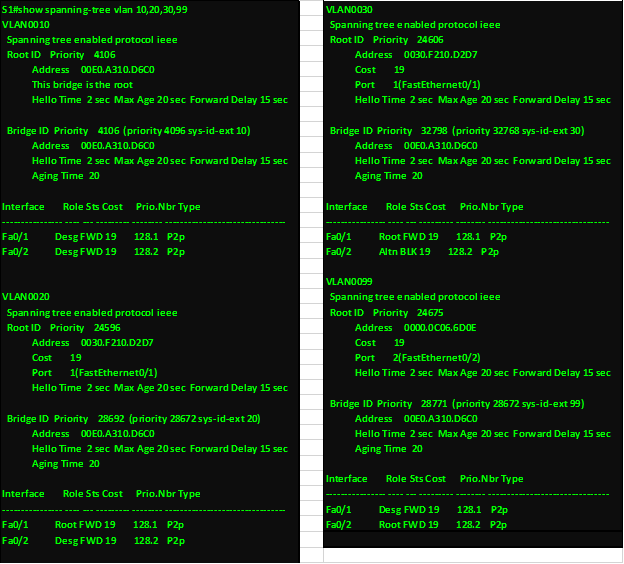
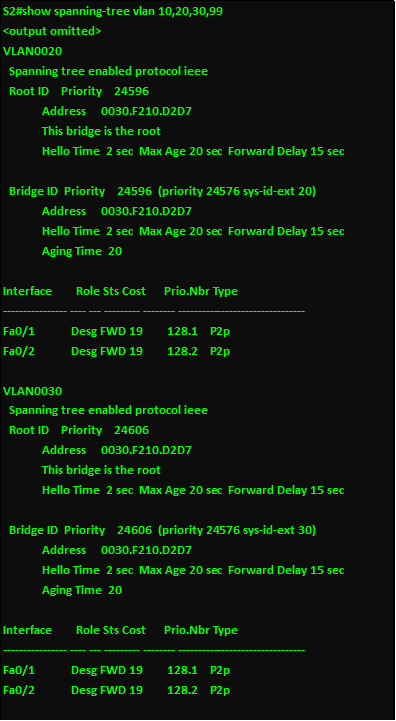
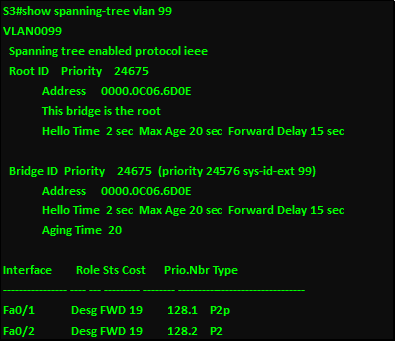
Overview
In the last chapter, we looked at frame relay and discussed its importance in the WAN. In this chapter, we will look at some network security concepts that are vital in today’s world. We will look at some of the risks as well as the ways we can secure our devices, we will also review security concepts we learnt in previous chapters.
Network security factors
In CCNA, we are supposed to familiarize ourselves with basic network security. The CCNA SECURITY course comprehensively covers the network security concepts that are needed in a small to medium size enterprise. In this chapter, we will look at the three factors that are crucial in networks, we will discuss what vulnerabilities we may have in our networks, the threats that we may face and some of the attacks. These factors are described below.
- Vulnerability – this are the weaknesses that we may have in the network. They may be as a result of the technology in use, the configuration on our devices or poor or weak security policies. In our networks, we need to plan for security carefully and consider these factors, a comprehensive security policy would be crucial in ensuring that data in our network is not accessed due to weak security on our devices.
- Threats – in network security, anyone who has the skill and the interest to manipulate any of the vulnerabilities, is known as a threat. These individuals or groups may be motivated by many factors such as money, power, and thrill seeking among others. Whatever the motive may be, threats to network security pose a major challenge for administrators since they may access information that is sensitive or even cripple the network.
- Attacks – these are the methods that are used by the threats to access the network. There are a number of attacks that can be used to access our network. They may be aimed at the network infrastructure through methods such as dumpster diving, or aimed at users using methods such as social engineering.
Securing the network
The security issues in the network are many and cannot be covered in one chapter, the various methods used by attackers to access networks have grave and far reaching effects, as such, we will focus on protecting routers and switches in this course. Some of the protection methods we will look at include:
- Physical security methods
- Passwords
- SSH
- Port security
Physical security
Physical threats to network devices are a major issue. Physical attacks may cripple an enterprise’s productivity due to outage of network services. The four classes of physical threats are:
- Hardware threats-damage to network infrastructure such as servers, routers and switches.
- Environmental threats– these are the threats that are brought about by storing the networking equipment in unsuitable places; the hardware may be subjected to extreme temperatures or extreme humidity.
- Electrical faults – the equipment that is used in our networks relies on electricity to work, as such, any sudden change in the electrical power supplied to the network devices is a major threat.
- Maintenance threats – from time to time, we may need to run maintenance checks on our network devices, the use of untrained technicians can pose a major threat to the network devices.
Some of the physical threats may be almost impossible to guard against. For example, we may not be able to predict an earthquake. However, we can effectively mitigate the threats to our network hardware by following the following guidelines:
Hardware threat mitigation
The location used for storing networking equipment as well the wiring closets, should only be accessed by authorized personnel. All the entrances should be secured and monitoring should be implemented by using CCTV cameras.
Environmental threat mitigation
The environment should be controlled to mitigate the environmental factors. the humidity, temperature, and other environmental factors should be monitored. The network control room should ideally be in a room where the conditions can be controlled effectively.
Electrical threat mitigation
The electrical threats may be mitigated by using UPS systems, so that the networking devices don’t draw their power directly from the mains. There should be backup systems such as generators and inverters so as to maintain network connectivity in case of power outage.
Maintenance threat mitigation
Maintenance threats should be mitigated by using well trained personnel. All the cables should be well labeled, maintenance logs should be maintained, and there should be availability of spare parts that are critical to maintaining connectivity.
Passwords
In the previous chapters, we discussed how passwords can be used to protect network devices, we looked at limiting access to the router and switch, console lines and telnet lines.
NOTE: passwords should be limited to administrators only, they should not be written down and should be changed regularly. A good password should contain a variety of characters.
Use of encrypted passwords is also better than passwords that have been stored in plain text.
SSH (secure shell)
We learnt that we can manage our routers and switches either locally using console and auxiliary ports on the router or remotely using virtual terminal lines.
Local access is the more secure way we can configure our routers, however, in some cases, we may not be able to access the network through the console port. For example, you may need to troubleshoot an issue on a router while you are on a trip.
Remote access gives us a more convenient way to manage an attacker, however, this may increase the vulnerability. For example, if we use plain text passwords, an attacker may capture packets that reveal the password.
Telnet is one way we can configure a network remotely, however, it is insecure since traffic is not usually encrypted. As such, we need to use a different protocol that will enable us to configure our network devices remotely in a secure manner.
The SSH protocol, is a management protocol that enables us to configure our devices securely in place of telnet. This protocol uses the TCP port 22.
We can use SSH to accomplish the following:
- Connect to the virtual terminal lines on a router so as to configure other devices securely
- Connect remotely and securely to a terminal server so as to make a specific configuration change
- Connect to modems attached to routers by dialing out securely
- Authenticate when making configuration changes by requiring passwords and usernames for each configuration line
Configuring SSH on Virtual terminal Lines
To enable SSH on a router, we must configure the following parameters.
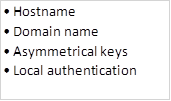
We can also configure the following optional configuration parameters:
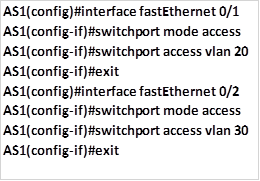
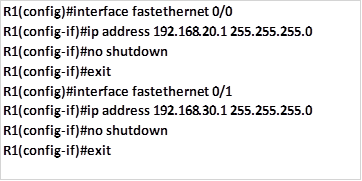
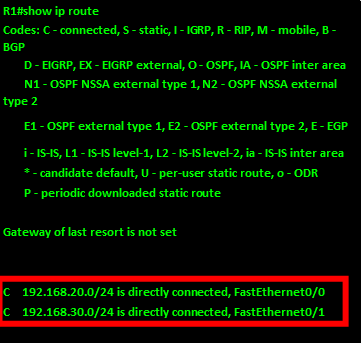
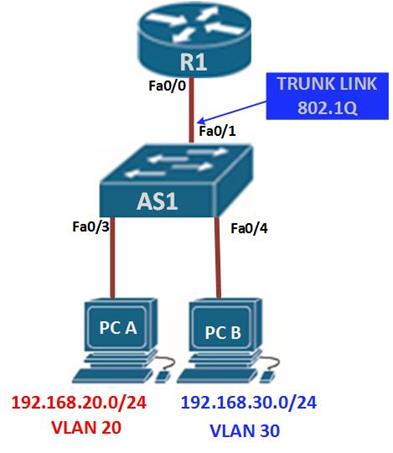
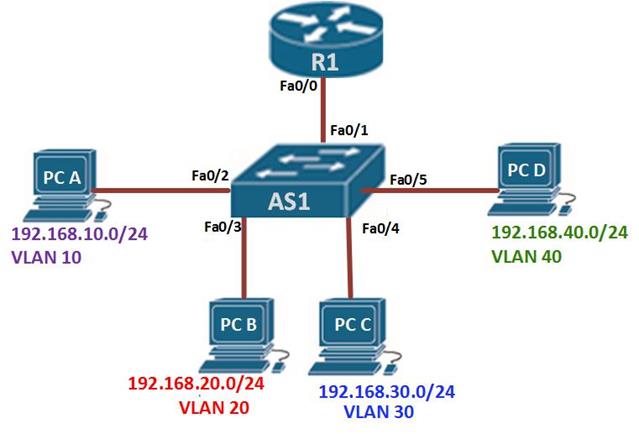
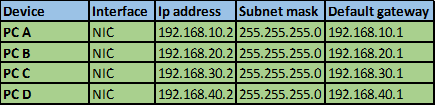
The diagram shown below shows the topology that we will use in this lab. The ip addressing has been configured and our task is to configure SSH on R2 so that users on R1 can only access it securely.
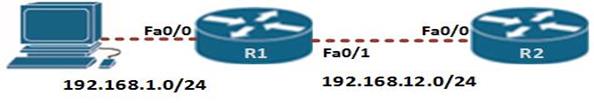
In this scenario, we will only be configuring R2 and the success of this lab will be determined when R1 can be able to access the console line of R2. Our configuration items include:

Step 1. Configure hostname
We need to configure the hostname to be used by the router using the command shown below in the global configuration mode.

Step 2: configure domain name
For SSH to work, we need to have a domain name. The command needed to configure a domain name is:

In our scenario, this command is implemented as shown below for a domain name called “cisco.com”

Step 3: Generation of the asymmetric keys
In SSH, we need to create a set of encryption keys that will be used to encrypt the SSH traffic. This is implemented in the global configuration mode using the command:

When this command is executed in a router, we are prompted to enter the size of the keys within a range of 360bits to 2048 bits. The longer the key the better the encryption, however, the longer our key the longer the time needed to create them.
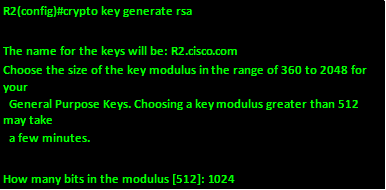
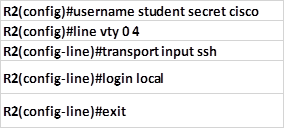
Step 4: the last compulsory configuration, is configuration of the local authentication which is done by configuring the username and a secret.
This is followed by implementing the SSH protocol on the virtual terminal lines. In our scenario, the username we will use is: “student” with the secret “cisco“. To activate SSH in the vty lines, we use these commands in the vty lines configuration mode:
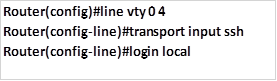
The command shown above, specifies that we are configuring 5 vty lines for SSH with the login mechanism being the local username and secret. The implementation of these commands in our scenario is shown below.
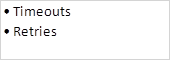
Step 5: Configure SSH timeouts (optional)
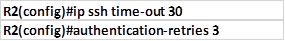
We can also specify the number of times that a person can try entering a password as well as how long they would have to wait if they get it wrong. This is optional and it is implemented using the commands shown below:
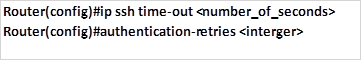
In our lab the SSH timeout is set to 30 seconds and the amount of retries to 3.
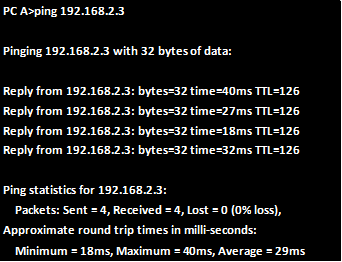
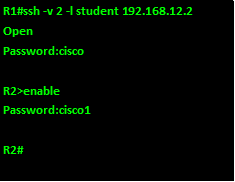
To test the remote terminal line connection, from R1, we use the following command:

The “-V” keyword specifies the version of configured on the remote router.
The username, and ip address or domain name are the remote router’s configured username and password.
After entering this command, you will be prompted for password for the SSH line.
After entering the VTY password you will be prompted for the router’s password and successful entry will gain you access.
The output below shows the access procedures for accessing R2 from R1.
NOTE: the passwords in this output have been shown but when accessing a real router, they will not be shown, and therefore it is imperative that you type in the password correctly.
NOTE: the process of login in remotely is a very important aspect and it is frequently asked in CCNA exams. It is therefore vital that you understand the security procedures for accessing a remote router.
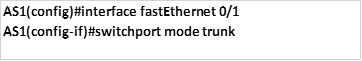
Port security
Port security is important in switch security. Unused ports are a major security issue since they can be used to attack the network. As discussed in the chapter on switch operation, securing switchports includes:

NOTE: the security concepts in CCNA are many and they are mostly covered in the security course, however, these concepts are crucial in securing a network.
Summary
In this chapter, we have looked at some of the security issues that affect the network, we discussed the security factors as well as the threats to network security. We then looked at various methods of securing the network and configured SSH as an alternative to telnet. In the next chapter, we will look at access control lists and discuss how they help in networks by adding security and traffic filtering.